Cloud computing has transformed how modern businesses build, deploy, and scale applications. From startups to enterprises, organizations rely on cloud platforms to deliver faster innovation and better customer experiences.
Cyber threats are becoming more sophisticated, and cloud environments are a prime target. Misconfigurations, weak access controls, and unsecured APIs can expose sensitive data and disrupt operations.
This practical guide from Compilex Technologies explains how to secure cloud applications effectively, using proven strategies that balance security, performance, and scalability. Also offers comprehensive DevOps solutions to help organizations deploy and secure their cloud applications.
Why Cloud Application Security Matters
Cloud applications handle critical business data, customer information, and intellectual property. A single vulnerability can lead to data breaches, financial loss, regulatory penalties, and damage to brand reputation.
Unlike traditional on-premises systems, cloud environments operate under a shared responsibility model. While cloud service providers secure the infrastructure, securing cloud applications remains the responsibility of the business.
Key reasons to prioritize cloud application security include:
- Increased attack surface due to remote access and APIs
- Growing compliance requirements (GDPR, HIPAA, ISO, SOC 2)
- Rise in cloud-native attacks such as credential theft and misconfigurations
- Business reliance on always-available digital services
Understanding the Cloud Shared Responsibility Model
Before implementing security controls, it is essential to understand who is responsible for what. Failing to secure the application layer is one of the most common cloud security mistakes.
| Cloud Provider Responsibilities | Customer Responsibilities |
| Physical data center security | Application security |
| Network infrastructure | Identity and access management |
| Host operating systems | Data encryption |
| Core cloud services | Configuration management |
Common Cloud Application Security Risks
Understanding threats helps in designing stronger defenses. Some of the most common cloud application threats include:
1. Misconfigured Cloud Services
Publicly exposed storage buckets, open databases, and insecure network rules are leading causes of cloud data breaches.
2. Weak Identity and Access Controls
Over-privileged users, shared credentials, and lack of multi-factor authentication (MFA) make it easier for attackers to gain access.
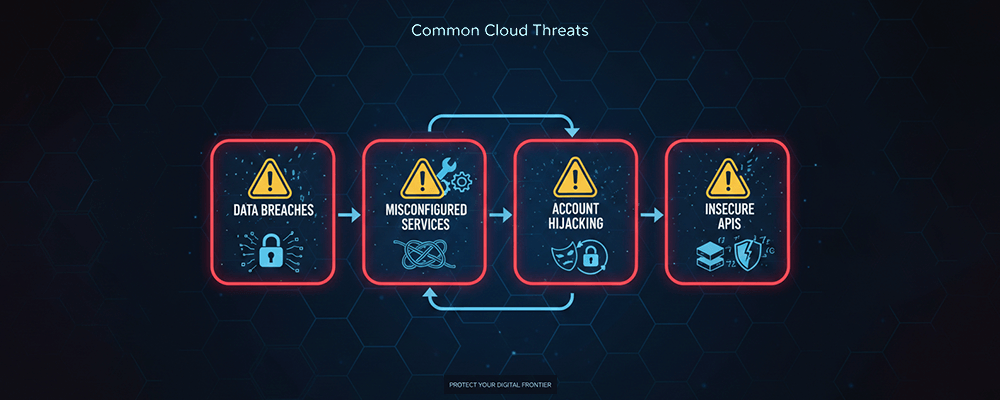
3. Insecure APIs
APIs connect cloud applications to services and users. Poor authentication or lack of rate limiting can expose critical data.
4. Data Breaches and Leakage
Sensitive data stored or transmitted without encryption is vulnerable to interception or unauthorized access.
5. Lack of Continuous Monitoring
Without visibility into cloud environments, security incidents can go undetected for weeks or months.
Cloud Application Security Best Practices
Securing cloud applications requires a layered approach that covers identity, data, development, and operations. Implementing the following best practices will significantly reduce cloud security risks.
1. Apply Strong Identity and Access Management (IAM)
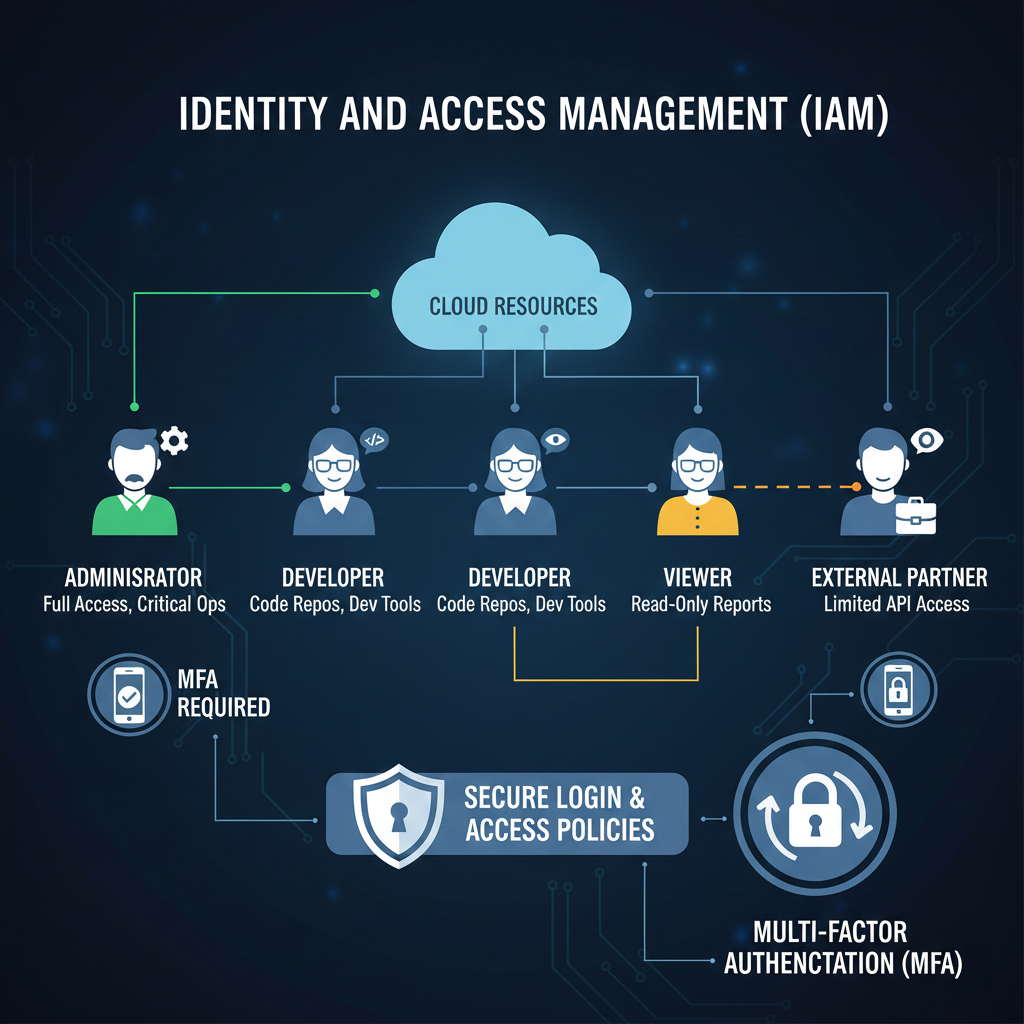
IAM is the foundation of cloud application security. By controlling who can access what, businesses reduce the risk of insider threats and compromised credentials.
Best Practices:
- Enforce least privilege access
- Use role-based access control (RBAC)
- Enable multi-factor authentication (MFA)
- Regularly review and revoke unused permissions
2. Secure Data with Encryption
Data protection is critical for securing cloud-based applications. Encryption ensures that even if attackers gain access, the data remains unreadable.
Key Security Measures:
- Encrypt data at rest using cloud-native encryption services
- Encrypt data in transit using TLS/SSL
- Manage encryption keys securely with Key Management Services (KMS)
3. Implement Secure Application Architecture
Security should be built into the application design, not added later.
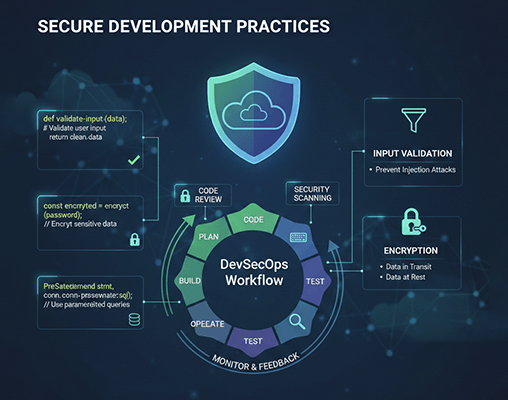
Architecture Best Practices:
- Use microsegmentation to isolate services
- Apply the zero trust security model
- Protect workloads with secure network configurations
- Avoid exposing services directly to the public internet
A well-designed cloud security architecture limits lateral movement during an attack. Compilex Technologies supports teams with secure custom application development and DevSecOps expertise to reduce application-level risks.
4. Protect APIs and Web Applications
Security should be integrated throughout the development lifecycle. DevSecOps reduces remediation costs and improves application resilience.
DevSecOps Practices:
- Perform automated security testing in CI/CD pipelines
- Scan code for vulnerabilities
- Monitor dependencies for known risks
- Fix security issues early in development
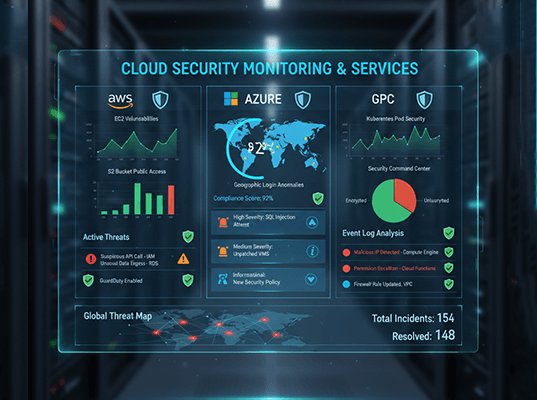
6. Continuous Monitoring and Threat Detection
Cloud environments are dynamic, making continuous monitoring essential. Early detection minimizes damage and speeds up incident response.
Monitoring Strategies:
- Enable centralized logging
- Monitor user behavior and access patterns
- Use cloud-native security tools for threat detection
- Set alerts for suspicious activities
7. Maintain Compliance and Governance
Compliance is a key aspect of cloud application security, especially for regulated industries. Strong governance ensures consistent security posture across all cloud assets.
Governance Best Practices:
Align security controls with industry standards
Document security policies and procedures
Conduct regular audits and risk assessments
Maintain visibility across multi-cloud environments
Cloud Application Security Checklist
Use this checklist to evaluate your current security posture:
- IAM with least privilege access
- Multi-factor authentication enabled
- Data encrypted at rest and in transit
- Secure APIs and web applications
- DevSecOps integrated into development
- Continuous monitoring and logging
- Compliance controls in place
How Compilex Technologies Helps Secure Cloud Applications
At Compilex Technologies, we understand that cloud security is not a one-size-fits-all approach. Our experts design and implement custom cloud security strategies aligned with your business goals.
Our Cloud Security Services Include:
We help businesses protect their cloud applications while maintaining agility and performance.
- Cloud security assessment and risk analysis
- Secure cloud architecture design
- IAM and access control implementation
- DevSecOps integration
- Compliance and governance support
- Ongoing monitoring and incident response
Future Trends in Cloud Application Security
As cloud technology evolves, so do security challenges. Staying ahead of these trends is essential for long-term cloud security success.
Key Trends to Watch:
- AI-driven threat detection
- Zero trust adoption
- Cloud-native security platforms
- Increased regulatory requirements
- Secure multi-cloud and hybrid environments
Final Thoughts
Securing cloud applications is no longer optional – it is a business necessity. By understanding risks, implementing best practices, and continuously monitoring cloud environments, organizations can protect their applications from evolving threats.
A proactive approach to cloud application security not only prevents breaches but also builds trust, ensures compliance, and supports business growth.
If you are looking to strengthen your cloud security posture, Compilex Technologies is here to help you secure, scale, and succeed in the cloud.









